Tag: IoT
Technological advancements - Balance between Earnings-Per-Share and Ethics-Privacy-Security
by RamaSundar K on July 9, 2018 2:21 am
Processing Power accelerating new technologies: AI/ML, Big Data and IoT Computing power is the driving force for recent advancements in AI/ML, Cloud Computing, BigData and IoT technologies. Tech companies are striving hard to maintain and expand their dominance in the tech field by using advanced processor technologies. For instance, Google has released its third-generation TPU… Read more Technological advancements - Balance between Earnings-Per-Share and Ethics-Privacy-Security
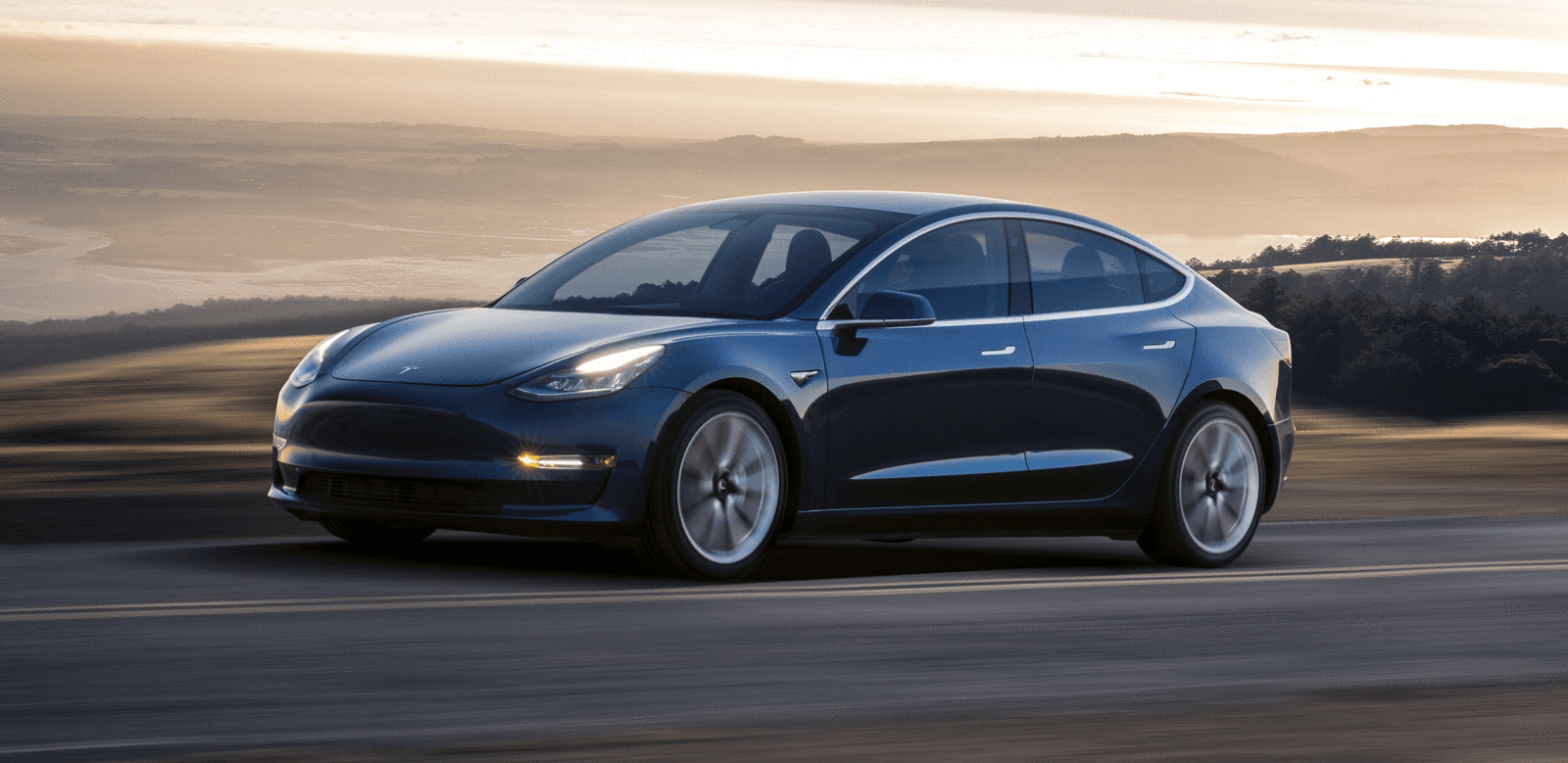
The future is here: My Model 3
by Boryana Dineva on July 31, 2017 5:08 pm
Tesla was founded 14 years ago, on July 1, 2003. The single goal that inspired both employees and the public was: Bringing a mass-market car to life. Through that, accelerating a sustainable energy future. Last Friday, July 28th 2017, a special event was held in the Tesla factory in Fremont, California. The first 30 cars… Read more The future is here: My Model 3
A game of cat and mouse
by Kam Fung on July 28, 2017 11:48 am
Let’s face it: Cybercriminals are constantly looking for new ways to tunnel into your network or disrupt your business. According to The State of Cyber Security 2017 survey, by ISACA, 53% of cyber security professionals reported an increase in the overall number of attacks in 2016 compared to 2015. In terms of the specific kinds… Read more A game of cat and mouse
Elements of Cyber Warfare: Examining The Way Forward
by Farhan Farooqui on July 28, 2017 10:49 am
Introduction From the Morris worm in 1988 to the 2017 presidential election, cyber intrusions and attacks have become common place in contemporary society. This is in large part due to our increasing reliance upon technology and computing to build and maintain our social, political and financial infrastructures. A single exploit into a government database or… Read more Elements of Cyber Warfare: Examining The Way Forward
Precious Loot: Healthcare Data
by Samuel Piotr Emch on July 28, 2017 10:25 am
In February 2015, the US health insurance Anthem Blue Cross announced the biggest data breach in the healthcare sector, even to this day. [1] Almost 80 million company records had been stolen. The hackers gained access to highly sensitive data like Social Security Numbers, birthdates and addresses. The Anthem case represents the tenacity that hackers… Read more Precious Loot: Healthcare Data
Automotive Cyber Security: Threat, Guidelines, and challenges
by Ramdev Canadam Sunder Rao on July 28, 2017 2:31 am
By 2020 it is estimated there will be 50 billion smart devices in use around the world or at least 7 connected devices for every man, women, and child on this planet. Also by 2020 projections are there will be 41 global megacities with a population about 10 million, with this it is very much… Read more Automotive Cyber Security: Threat, Guidelines, and challenges
Sensor Data and Mars-Drilling
by Christopher Hoftun on July 27, 2017 7:47 pm
Introduction Drilling is anticipated be an important activity in the future exploration of Mars. Its primary motivation will be to allow the exploration of the subsurface of Mars, in particular to search for, and eventually study, life on Mars. The scientific value by acquiring in situ samples for analysis is one of the primarily objective… Read more Sensor Data and Mars-Drilling
IoT devices and DDoS attacks
by Nicolas Andre Wahl on July 26, 2017 11:35 am
Last Friday, Steve Herrod, Managing Director of General Catalyst, warned us about the dangers of the lack of security of the Internet of Things (IoT), namely all the poorly secured devices which are part of it. Indeed, hackers can hijack most of these devices, and then to turn this Internet of Things into a real… Read more IoT devices and DDoS attacks
Hardware Level Security
by Ajit Punj on July 25, 2017 9:00 am
In this week’s lecture, Dr. Stephen Herrod mentioned the importance of cyber-security. Data storage is sensitive, and security of that data is very important. In addition, more and more data is being stored online including health records, etc. Stephen also mentioned how cyber attacks are becoming more sophisticated by using massive public cloud resources, hijacking the internet of things to create… Read more Hardware Level Security
Next-Generation Firewalls: Intelligent Threat Analytics in Cyberspace
by Christian J. Estes on July 25, 2017 12:06 am
Introduction During our lecture with Dr. Stephen Herrod, he had outlined the significance of Cybersecurity in the era of Cloud Computing, Big Data, Artificial Intelligence and IoT. As Dr. Herrod indicated during our lecture, the potential impact and cost of a breach in security can lead to severe repercussions. When Target was hacked through their… Read more Next-Generation Firewalls: Intelligent Threat Analytics in Cyberspace