Automotive Cyber Security: Threat, Guidelines, and challenges
By 2020 it is estimated there will be 50 billion smart devices in use around the world or at least 7 connected devices for every man, women, and child on this planet. Also by 2020 projections are there will be 41 global megacities with a population about 10 million, with this it is very much clear that there will be an exponential growth in usage of cars and ride sharing worldwide.
Latest innovations in cloud computing, internet of things (IoT), deep learning has made cars as a connected device.
While all these advancements in the technology create new exciting opportunity, it also creates challenges. One of the issues is “Cyber Security”, which is also the foundation of every technology.
Figure 1: Cover of NHTSA’s new auto cybersecurity guide (source [1])
Factors Contributing to Cyber security risks in the automotive industry:
Mary Barra Chairman, CEO of General motors in her key note at Global automotive cyber security says, three major factors which are contributing to the cyber security risks are
- Internet of Things – lead the growth in vehicle connectivity
- Content-Fact that personal data is increasingly stored, transmitted through the vehicle network
- Complexity-In 2000’s cars had an average of about 1million lines of code, and today cars have an average of 100 million lines of code that is more than F35 fighter jet! This definitely opens up opportunities to those who want to harm through cyber attacks
What kind of threat that one can expect in the automotive industry:
Threats require physical access to a car or it can be done over the air. Before we go over type of threats that can happen on a vehicle, I would like to shed some lights on inner details of today’s modern vehicles available in market
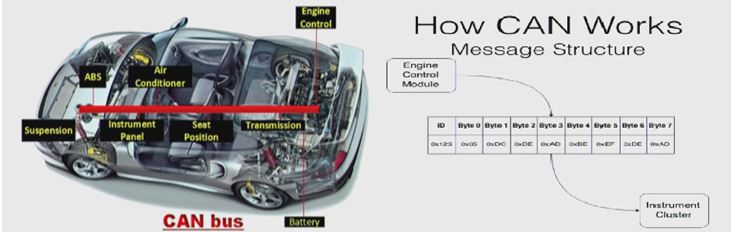
A lot of control over vehicles, lot of sensors and computing power made “cars are computers”. In the USA you can only sell a big SUV or a truck if it is available at reasonable prices, and more over it should consume less gas and fewer emissions. This is where automakers started to bring the compute capability in the cars to achieve better performance. Also “cars are networks”, modern vehicles have electronic control units (ECU’s), connected to a controller area network (CAN) bus, which acts as the master and can broadcast messages between ECUs.
Figure 2: CAN bus on today’s car (Source [2])
CAN is a trusted network, and once you are on CAN you can modify the functionality of a vehicle by sending messages to ECU’s, and today CAN is not typically secured!
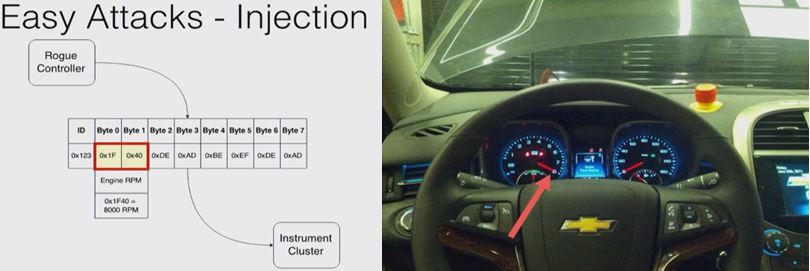
One of the easiest attacks which some one can do is on CAN by injecting messages. Since all the traffic is visible to all controllers, and any controller can send any messages over CAN. For example, you could intentionally attach a device or some remote exploit on a head unit which is connected to the internet, with that one can send messages over CAN that can damage the vehicle. This may be a simple example of an attack.
Figure 3: Simple attack by hacking CAN bus (source [2])
The other vectors which causing the threats are, originally we had one compute engine which used to control the car and one diagnostic port under the hood, today we have Bluetooth, wife, 4G network, CDs, USBs, media players and list goes on and on. A case paper from autosec http://www.autosec.org, in 2010 explained threats via CD, PassThru, Bluetooth, and Cellular. And one of the coolest exploits was calling to a car by using the public phone number, and play a song into the phone at the same time they had a special modulated audible part of the spectrum which sending some messages to the CAN bus to take the control of the vehicle! The below picture captures some of the results with this hacking reported in this case paper.

Figure 4: Case Paper describing the results achieved by sending different malware packets to CAN bus (source [2])
A widely publicized incident reported In July 2015, famed car-hackers Charlie Miller and Chris Valasak had remotely assumed control of the vehicle through its Uconnect system, a vulnerability which caused Chrysler to issue a recall for 1.4 million cars (Wired). What actually happened is: There was a Harmen head unit on this vehicle which does all radio features, like access to internets, access to infotainment system in the car etc. This head unit is running on Linux and using D-Bus (which is inter-process communication mechanism in Linux) on wifi cellular on an open port which allowed anonymous authentication. Linux was connected to V850 microcontroller and this micro controller connected to CAN, they have just changed the code on V850 which got them control over CAN. More details available at http://illmatics.com/Remote%20Car%20Hacking.pdf
Guidelines for Automotive Cybersecurity Best Practices:
The members of the Alliance of Automobile Manufacturers (“Auto Alliance”) and the Association of Global Automakers (“Global Automakers”) have collaboratively developed Framework for Automotive Cybersecurity Best Practices, which is intended to support the ongoing efforts of the automobile industry on cyber security matters, the framework guiding principles are:
- Vehicle security by design-The automotive industry is incorporating security into the vehicle development process, including by designing security features into hardware as protective functions for vehicle control system and communications-based functions like navigation satellite radio, and telematics, and using “threat modeling” as a design process to both test systems for vulnerabilities and simulate attacks to test security and design controls.
- Risk assessment and management-Risk assessment and management strategies can help assess the potential impact of identified cyber security risks and discovered vulnerabilities and assist in the development of protective measures.
- Threat detection and protection-This principle complements defenses obtained through security by design that is intended to stop cyber-attacks before they impact a system
- Incident response– A comprehensive response plan that develops increased awareness and capabilities and that establishes communications protocols between automotive manufacturers, suppliers, cyber security researchers, and government agencies.
- Collaboration and engagement with appropriate third parties– Members of the Auto Alliance and Global Automakers to engage with third parties, including peer organizations, suppliers, cyber security researchers, government agencies and the Auto-ISAC. This will include working with suppliers to ensure the appropriate utilization of cyber security measures and maintaining clear communication channels.
To Sum up, Today with an unprecedented wave of innovation, automakers are pioneering groundbreaking technologies that are bringing more advanced features in the cars ever before, but there are many challenges emerging along the side of this wave of innovation, among which cyber security is most important one. So every car makers are considering cyber security as a top priority, and proactively and collaboratively working towards addressing potential challenges in cyber security, mitigating risks by producing safe vehicles that incorporate modern and robust security protection.
References:
[1]http://www.bankinfosecurity.com/feds-propose-voluntary-automotive-cybersec-standards-a-9482
[2] https://www.youtube.com/watch?v=t6qTEiLt1hs
[4] https://www.youtube.com/watch?v=DX7zhS_W8d0
[5] http://automotivecybersecurity.iqpc.com/media/1003028/71042.pdf
Users who have LIKED this post:
2 comments on “Automotive Cyber Security: Threat, Guidelines, and challenges”
Comments are closed.


Great in-depth article on auto cyber security! In a day and age where autonomous vehicles are becoming more and more of a reality, I definitely believe that auto cyber security is an underrated aspect of this growth area. In fact, it was not till earlier this year that auto cyber security saw serious attention in legislative matters. There was finally a bipartisan bill that was introduced to the House of Representatives that was intended to outline what kind of hardware and software packages in automobiles needed solid firewalls or general protection and what this protection looks like etc. (source: https://arstechnica.com/cars/2017/01/worried-about-cybersecurity-and-the-connected-car-theres-a-bill-for-that/) It will be interesting to see how much more developed such regulations will get once autonomy and vehicle connectivity proliferate.
Users who have LIKED this comment:
Thanks Abhishek for adding an important point on how the government is involving to control auto cybersecurity, good to know this.
Regards
Ramdev