Cybersecurity and Wearables
What Is Cybersecurity?
Cybersecurity is the body of technologies, processes and practices designed to protect networks, computers, programs and data from attack, damage or unauthorised access [1]. With continuously evolving technology, threats are advancing faster than the cybersecurity advancements being made. Cybercriminals aim to exploit weaknesses within a system, and this has turned cybercrime into a multibillion dollar industry [2]. To emphasise the importance of cybersecurity, the US federal government has allocated over $13 billion a year to tackle this problem.
Cybersecurity can be broken down into 3 key areas [2]. The first is cyber terrorism, which is about terrorist groups furthering their ideological/political agenda through attacks on networks and telecommunication infrastructures. The second is cyber warfare, which is often acknowledged as the fifth domain of warfare (after the more commonly known land, air, sea, space). Cyber warfare involves nation-states penetrating the networks of other nations to cause damage/disruption. The third is cyber espionage, which involves obtaining secret information about someone/something, without permission.
How Is An Attack Carried Out?
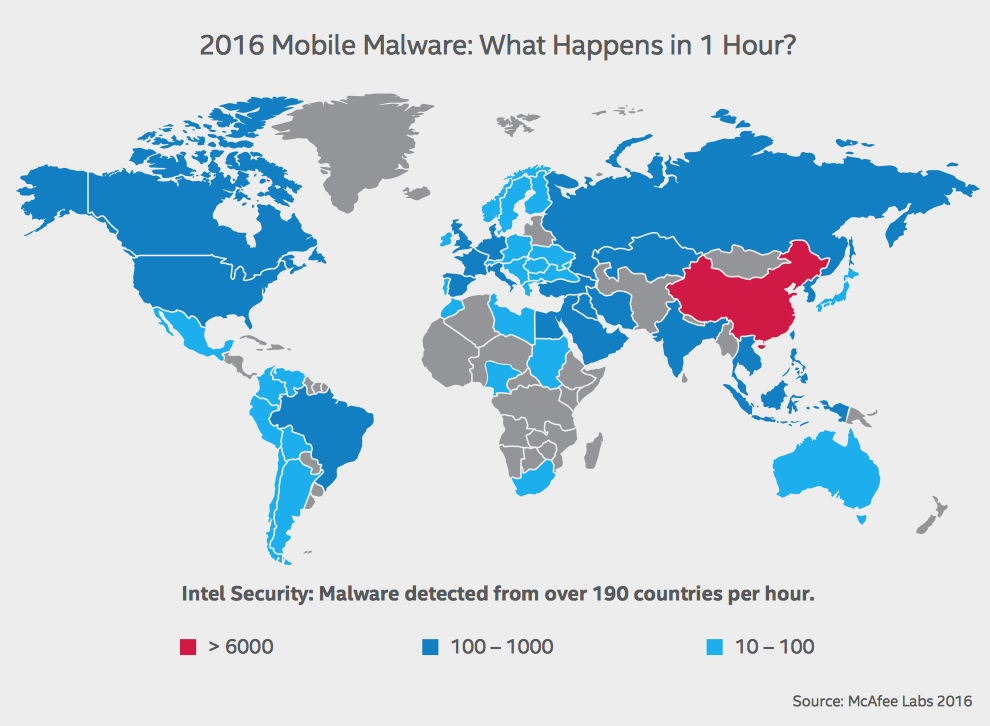
You must be wondering how all of these attacks are carried out? Cyber criminals often use malware and vectors to attack their victims [3]. Malware is a software designed to damage/gain access to a computer system and can be executed in the following ways. Ransomware (which has frequented in the news recently) is a malicious program that demands payment after launching an attack. Viruses are small pieces of code that replicate and spread across multiple computers, by attaching to another computer file. Worms are self-replicating and do not need a program to be attached to. Instead, they search for weaknesses and report back to the worm creator when a vulnerability is discovered. Spyware/adware infects your computer when you open an email attachment or click an infected link – which installs the malware straight on to your system. Finally, a Trojan virus operates through a façade, by appearing to perform one function (e.g. remove viruses from your computer), but actually doing something malicious behind the scenes. The graph below shows the spread of malware across the world [4]:
The Impact On Wearables
Wearable technology has recently become mainstream, with the likes of Apple Watch and Fitbit, resulting in privacy/security issues arising. Wearables can be classified into 4 categories: smart glasses and headgear, smart watches, wearable medical devices and fitness trackers. All of these categories share 3 main features: sensing and translating data, collecting and preparing data for transmission, and transmitting data to off-site storage for processing and reporting [5]. Many of these devices are network connected, and continuously stream critical data to the cloud. But proper protection measures have not been implemented, with current encryption software needing to be strengthened – according to a cybersecurity expert from security firm PKWARE [6].
There are a few aspects of wearables that pose serious security concerns [7]. Many wearables store data on the local device, without any encryption. Accessing data on a wearable often does not require any sort of user authentication, and this opens up hackers to personally identifiable information (PII). Another key issue is with wireless connectivity, since wearables connect to smartphones and other devices via Bluetooth, NFC and Wi-Fi – which cannot guard against a brute-force attack. There is also a lack of policy to cater for wearables. Our laptops/desktops receive patches for the latest vulnerabilities, but wearables run their own operating systems/applications – and as they become more common, they will become a bigger target for hackers.
References
[1] http://whatis.techtarget.com/definition/cybersecurity
[2] https://www.paloaltonetworks.com/cyberpedia/what-is-cyber-security
[3] https://www.itgovernance.co.uk/what-is-cybersecurity
[5] https://www.abbb.com/enewsletter/article/technology-wearable-technology-cyber-security-threat
[6] http://www.cnbc.com/2015/07/24/wearables-are-the-next-big-cyberthreat-expert.html
2 comments on “Cybersecurity and Wearables”
Comments are closed.


Greetings Jay,
It was a very interesting and insightful blog post on the topic of cybersecurity. I wrote a blog post on why this field is increasingly getting harder and some of the points you mentioned here such as the wearable technology just further highlights the issue of having new ways to hack almost everyday. Let me know your thoughts in this regard!
Hey Jaykishen, this was a good read.
This brings to the surface another issue- wearables threatening cyber security in the work place. As you mentioned, the main problem with wearables is the inherent lack of security. While most companies go to significant lengths to keep enterprise software secure, this isn’t always the case with wearables; IoT manufacturers haven’t been approaching security design with the same experience and perspective. In addition, the emphasis is often placed on design and aesthetics, rather than security. Since this technology is arguably still in its infancy, security is lagging behind – ultimately creating a number of considerable concerns for businesses. In fact, the Traveler’s Business Risk Index of 2015 found that 58% of US businesses worry somewhat about cyber risks/breaches posed by wearables, and 23% worry a great deal.