Tag: CyberSecurity
Cybersecurity: Industrial Control Systems and the U.S. Electric Grid
by David L Love on July 26, 2017 7:19 pm
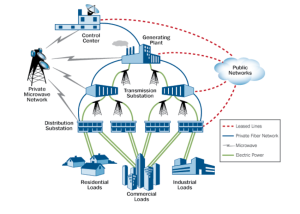
The U.S. electric grid, critical to supporting modern conveniences and enabling the enjoyment of a high standard of living, is dependent on a layered grid architecture including generation of power, transmission over two hundred thousand miles of power lines, and distribution to businesses and residences.1 When originally established, generation was accomplished via mechanical devices and processes… Read more Cybersecurity: Industrial Control Systems and the U.S. Electric Grid
Trust me, I’m a medically trained device
by Lana Hampicke on July 26, 2017 11:29 am
On the morning of the 27th of June 2017, Stanford Medicine and Duke University School, welcomed a few volunteers into their offices. Every participant had to sign a consent form before they could collect two devices that will monitor their biomedical stats for the next few years (heartbeat, activity, sleep pattern etc.). The project is… Read more Trust me, I’m a medically trained device
Cybersecurity spring cleaning!
by Boryana Dineva on July 26, 2017 9:56 am
Cybersecurity is like exercise, we all know we should be doing more of it but most of us do the bare minimum. Guilty! Almost every single one of our speakers to date touched upon a different angle of information cybersecurity. Each underlined the importance of it – from the Government and public service obligation perspective,… Read more Cybersecurity spring cleaning!
Next-Generation Firewalls: Intelligent Threat Analytics in Cyberspace
by Christian J. Estes on July 25, 2017 12:06 am
Introduction During our lecture with Dr. Stephen Herrod, he had outlined the significance of Cybersecurity in the era of Cloud Computing, Big Data, Artificial Intelligence and IoT. As Dr. Herrod indicated during our lecture, the potential impact and cost of a breach in security can lead to severe repercussions. When Target was hacked through their… Read more Next-Generation Firewalls: Intelligent Threat Analytics in Cyberspace
Security in a Brave New World
by Aaron Loh on July 24, 2017 1:38 pm
You’re working in a hotel lobby of a conference, connected to a wireless hotspot, comfortably surfing the web. Email is open in one tab, your personal cloud storage in another. You’re logged in to your company portal, checking your paystubs. You hear a beep behind you. You turn, and find yourself face to face with… Read more Security in a Brave New World
Applications of Machine Learning to the Finance Industry
by Adeesh Goel on July 21, 2017 11:37 am
Background: Being highly data-driven, finance is one of the initial industries that began applying data science methods to optimize functioning. Some of these applications include, optimizing the interest rate gap between the interest charged for loans, and the interest paid for deposits to maximize long-term profitability; or using machine learning to target the marketing of… Read more Applications of Machine Learning to the Finance Industry
A Shift Towards Cloud Computing
by Christopher Hoftun on July 7, 2017 2:07 pm
Mr. Chris Cruz, Chief Information Officer (CIO) for the state of California shared his views on Cloud Computing for transparency to foster sharing and pooling of computing resources in the public sector. Mr. Chris Cruz talked about how the state of California´s motivation on transparency and its engagement towards it´s citizens to unlock government data… Read more A Shift Towards Cloud Computing
Law Enforcement Agencies
by Lana Hampicke on July 7, 2017 6:53 am
As the world gathers this weekend in Singapore for the Annual Interpol World Congress to discuss law enforcement cooperation, we are all reminded of the impact of AI/IoT/Cloud/Big Data technology in advancing law enforcement. The policing landscape is changing very fast: the summary below looks at covering some of the emerging trends in law enforcement.… Read more Law Enforcement Agencies
How Secure is a Connected Car from a Cyber Threat?
by David L Love on July 7, 2017 5:55 am
With wireless technology rapidly shifting toward fifth generation (5G) capability, the connection of consumer-oriented devices to the internet will expand exponentially. One interesting application area that 5G technology enables is the furtherance of the Intelligent Transportation System (ITS) concept.1 ITS can support vehicle-to-vehicle (V2V), vehicle-to-infrastructure (V2I), and infrastructure-to-vehicle (I2V) communications, thus enabling the transportation industry to begin realizing a vision supported by autonomous… Read more How Secure is a Connected Car from a Cyber Threat?
Transparency and Innovation in California:
by Victor Gardrinier on July 6, 2017 5:53 pm
Dr. Daniel Barreto introduced the CIO’s objective in a company by saying that a CIO should “power a competitive business full of opportunities and challenges.” Ambiguity and paradoxical situations are part of the job description as the CIO must balance between Cybersecurity issues, regulation compliances, and transparency. Two separate issues that are hard to associate… Read more Transparency and Innovation in California: