David L Love
Posts by David L Love
Big Data and Pre-emptive Services in Wireless: Improving Performance at the Edge
by David L Love on August 4, 2017 5:25 am
To build on previous posts discussing what the wireless network of the very near future will deliver and enable, one area requiring exploration is artificial intelligence and how that can be used to improve network performance, particular at the edge. With current Long Term Evolution (LTE) fourth generation (4G) wireless networks, remote radio units (RRUs)… Read more Big Data and Pre-emptive Services in Wireless: Improving Performance at the Edge
Cybersecurity: Industrial Control Systems and the U.S. Electric Grid
by David L Love on July 26, 2017 7:19 pm
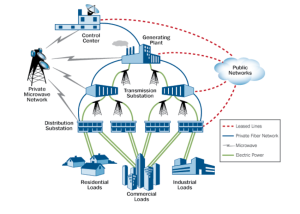
The U.S. electric grid, critical to supporting modern conveniences and enabling the enjoyment of a high standard of living, is dependent on a layered grid architecture including generation of power, transmission over two hundred thousand miles of power lines, and distribution to businesses and residences.1 When originally established, generation was accomplished via mechanical devices and processes… Read more Cybersecurity: Industrial Control Systems and the U.S. Electric Grid
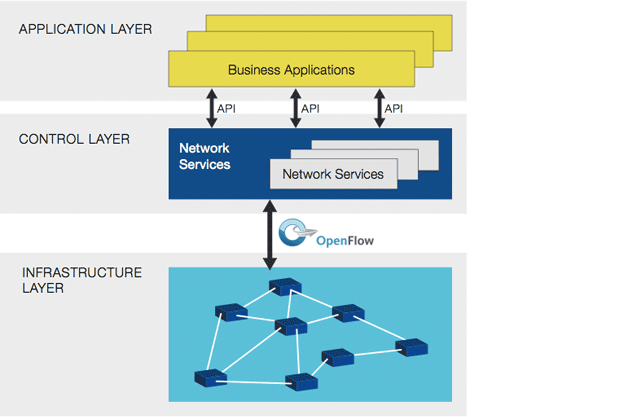
Wireless Evolution, Software Defined Networks and Network Function Virtualization: Enablers of IoT
by David L Love on July 20, 2017 6:54 pm
Having worked with several Tier 1 wireless carriers closely as customers since 2008, I found John Donovan’s clear explanation of market challenges to be outstanding. As he noted, AT&T and Apple had an exclusive relationship for the iPhone from inception, and the company’s proven history with long-term research has shown their commitment to delivering a… Read more Wireless Evolution, Software Defined Networks and Network Function Virtualization: Enablers of IoT
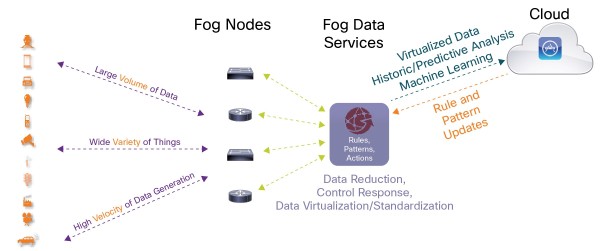
Fog Computing: Extending the Cloud?
by David L Love on July 14, 2017 7:32 am
In the past ten years, the usage of cloud-based systems to build applications and store data has exploded. As Dr. Jeff Welser of IBM discussed in his presentation on 7 July 2017, the amount of computer power at the edge of the internet exceeds that of all the computers in all the world’s data centers.… Read more Fog Computing: Extending the Cloud?
How Secure is a Connected Car from a Cyber Threat?
by David L Love on July 7, 2017 5:55 am
With wireless technology rapidly shifting toward fifth generation (5G) capability, the connection of consumer-oriented devices to the internet will expand exponentially. One interesting application area that 5G technology enables is the furtherance of the Intelligent Transportation System (ITS) concept.1 ITS can support vehicle-to-vehicle (V2V), vehicle-to-infrastructure (V2I), and infrastructure-to-vehicle (I2V) communications, thus enabling the transportation industry to begin realizing a vision supported by autonomous… Read more How Secure is a Connected Car from a Cyber Threat?
RECENT POSTS
Recent Comments
- Joshua Ching on Blockchain + AI
- Joshua Ching on IoT and AgTech
- ccjw on Why Investors Really Care about Impact Investing
- ccjw on Why Investors Really Care about Impact Investing
- ccjw on Blockchain + AI
Categories
- summer2017 (277)
- Uncategorized (9)
- Week1 (48)
- Week2 (49)
- Week3 (49)
- Week4 (45)
- Week5 (48)
Tags
Executive with over 30 years information systems and technology experience. I have worked in wireless/mobility since 1995, including customer care, billing, prepaid, network operations, hosting operations, mobile content delivery, streaming video, and emerging technologies. I am a licensed Professional Engineer, holding a Ph.D. in engineering management, an M.S. in physics, an M.S. in nuclear engineering, and a B.S. in physics/mathematics. Views expressed are my own.