
IoT Security: Big Opportunities from Billions of Devices
Internet of Things (IoT)
The Internet of Things (IoT) is a system of interrelated computing devices, mechanical and digital machines, objects, animals or people that are provided with unique identifiers and the ability to transfer data over a network without requiring human-to-human or human-to-computer interaction.

The rapid rise of a new generation of connected, intelligent devices — collectively known as the Internet of Things or IoT presents vast opportunities for organizations to improve internal efficiencies, serve customers better, enter new markets, and even build new business models.
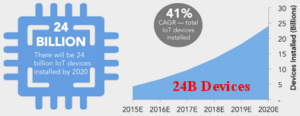
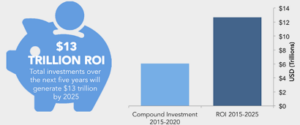
It has been predicted that there will be 24 billion IoT devices installed by year 2020 (41% CGAR), which is equivalent to 3.5 to 4 devices per person in the entire world. About $6 Trillion will be invested on IoT devices with the expectation of $13 Trillion in ROI. Most investments are happening in the Application Development, Hardware, System Integration & Storage compared to Security, it is a huge concern as well a big opportunity.
Some Insights!
$– The economic impact of the Internet of Things will be measured in $trillions.
∑ – The number of connected devices will be measured in billions.
∞ – The resultant benefits of a connected society are significant, disruptive and transformational.
The rapidly growing connected world exposes to a massive attack through everyday vulnerabilities in IoT are being exploited with malicious content, which can be mitigated.
IoT Disruption: IoT can improve internal efficiencies, serve customers better, and even build new business models. High volume of IoT devices is coming online and has increased our exposure to cyber threats. Security in IoT devices and their connecting networks is key to assess early. We are still early in a current IoT protection framework for implementation of this technology. Today, to prevent rogue commands and communications or data leakage is a much-needed priority. The DDoS attack against Dyn from 2016 was an exposed to come from connected devices.
Business Opportunities: IoT security requires a multilayered approach. There are opportunities to secure the communication at all layers. We see an evolving opportunities in one of the following areas.
- Assessing the business risk
- Data and connected device protection
- Business needs to align IoT strategy and security
- Solving regulatory and legal issues
Emerging Security spotlights
Connected car
The potential for a hacker to unlock and enable a car’s ignition or remotely take over mission-critical systems — brakes, steering, transmission — has caught the attention of consumers, manufacturers, and legislators.
Industrial Devices
Protect data about manufacturing operations and to prevent unauthorized access to interconnected networks and facilities.
Health Monitoring Data
Patient information is already a favorite target of cybercriminals.Beyond data vulnerability, the risk of outsiders taking control of some devices has critical health implications
Early stage and emerging companies creating big opportunities from billions of devices.
| Company | Space | Year | Investment | Location | Information |
| Zitovault | Smart Homes, Industrial IoT | 2016 | Un-disclosed | California | Company’s patent protected software focuses on scalability while maintaining a lightweight footprint on the client’s side |
| Karamba Security | Automobile IoT | 2015 | $5M | Michigan, Israel | IoT Security solution called “Carwall” that targets the Electronic Control Units (ECUs) within automobiles and ensures that all cars are protected |
| Argus Cyber Security | Connected Automobile | 2013 | $30M | Israel | Embedded or aftermarket based, already supports advanced safety features and improved passenger experience which will enable the autonomous car. |
| Thetaray | Finance Service & Industrial Internet | 2013 | $25M | Israel | Develop a security solution that uses machine learning and big data to identify anomalies in all kinds of domains. |
| ZingBox | Healthcare, Industrial Internet | 2014 | $1.5M | Silicon Valley | Targets healthcare and the industrial internet. uses machine learning to automate device discovery, network behavior profiling, and anomaly detection. |
| Trillium | Automobile | 2014 | Undisclosed | Japan | 2015 they delivered their IoT security platform called “HeavenZ” to an automotive Tier One and consumer OEM |
| Mocana | Mobile Security | 2004 | $65M | SFO | Over 200 major globally-recognized OEMs have integrated Mocana security into their offerings. None of the Company’s engineering is outsourced overseas for security reasons and the platform supports 35 operating systems and 70+ CPUs. |
| Indegy | Industrial Control Systems Network | 2014 | $18M | Israel, Palo Alto | Indegy platform provides visibility and control over ICS networks, an area that 92% of manufacturers are concerned about. |
Do above companies would ever have the technology to secure IoT, given the volume of devices and given the distributed nature of devices, is it even possible to recover from IoT security breaches if they occur?
We anticipate government involvement / regulations to manage and control IoT security threats and introduce specific standards in this space to best way to secure IoT devices
References
[1] https://iotsecurityfoundation.org/
[2] https://securityintelligence.com/lessons-from-the-dyn-ddos-attack/
[3] https://www.vlab.org/events/iot-security-high-stake-billions-devices/
[4] https://www.business.att.com/cybersecurity/archives/v2/executive-summary/
[5] http://internetofthingsagenda.techtarget.com/definition/Internet-of-Things-IoT


