
Next-Generation Firewalls: Intelligent Threat Analytics in Cyberspace
Introduction
During our lecture with Dr. Stephen Herrod, he had outlined the significance of Cybersecurity in the era of Cloud Computing, Big Data, Artificial Intelligence and IoT. As Dr. Herrod indicated during our lecture, the potential impact and cost of a breach in security can lead to severe repercussions.
When Target was hacked through their HVAC vendor, there were several questions about Target’s level of security. It’s unclear why Target would have given an HVAC company network access to a segment of the network connected to Target’s payment system network. As Cybersecurity threats become more prevalent, executives like Gregg Steinhafel (Former CEO of Target) need to take precautions to ensure that customers financial data is protected. While it’s unfortunate that Steinfeld was forced to resign as result of the breach, organizations like Target are cracking down on loosely implemented security polices. As attacks vectors grow, and the attacks themselves become more sophisticated, it’s important for security professionals to create intuitive security policies in accordance to industry standards and security domains.
Figure 1 – CIA Triad for Cloud Computing
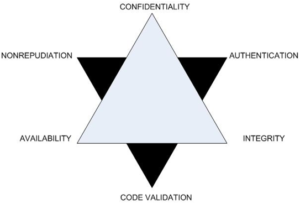
(IS Buzz News, 2017)
The CIA Triad for example states, “The goals of information security are to ensure the continued Confidentiality-Integrity-Availability of an organization’s assets. This includes both physical assets (such as buildings, equipment, and, of course, people) and information assets (such as company data and information systems). Access controls play a key role in ensuring the confidentiality of systems and information. Managing access to physical and information assets is fundamental to preventing exposure of data by controlling who can see, use, modify, or destroy those assets.” (Gordon, 2015)
With Big Data, code validation is a HOT topic. Bad programming practices often lead to vulnerabilities and could make you a potential target. Data has become a valuable commodity on the Black market. Hackers are developing Ransomware to hold your data hostage and even after you have paid, what’s say your data isn’t bought and sold or even given away to someone else that wants to extort you for more money. As Big Data, Cloud Computing, and IoT become more widely adopted and used by organizations, Code Validation-Authentication-Nonrepudiation have been added to the Triad
Next-Generation Firewalls (NGFW)
While the creation of security policies and practices is important, having knowledge of what do and being able to react to threats are different. As software threats like malware become more intelligent and polymorphic (See Definition) in nature, IT teams specializing in security need to implement Advanced Threat Intelligence using Application Visibility and Control (AVC) which inspects traffic at the Application Layer (E.g. Layer 2 through Layer 7 of the OSI model).
Polymorphic malware for example, is software that behaves like a virus, worm, Trojan or spyware that constantly changes (“morphs”), making it difficult to detect with anti-malware programs. This level of intelligence at a software level requires the use of Machine Learning functions that evaluate the payload of the packet and look for patterns across several packets that my present a threat. (Tech Target, 2017)
Security professionals also need to implement Intrusion Prevention mechanisms using algorithms that sandbox potential threats by executing code and creating real-time signatures for Zero-Day attacks. According to Gartner, Cisco Systems, and Palo Alto Networks are both leaders within this industry and utilize Advanced Threat Intelligence, Dynamic Signature creation and Defense mechanisms using AI/ML in the Cloud to mitigate against malicious code. (KrebsonSecurity, 2013)
Figure 2 – Cisco VM Cloud Security Pillars and Compliance Analytics
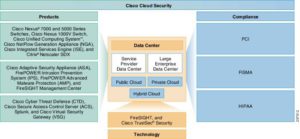
(Image Courtesy of Cisco)
Compliance for Cybersecurity Insurance
When deploying Cisco Firesight Manager with Cisco’s NGFW solution, security managers and policy makers have the ability to utilize Firesight Manager to ensure that they’re in compliance with standards as defined by governing bodies like PCI or HIPAA. As Dr. Herrod mentioned during his presentation, CyberSecurity Insurance is a new trend in the market, however, it’s been difficult for insurance providers to gauge compliance of Public, Private or Hybrid Cloud infrastructures. (Cisco Systems, 2016)
Figure 3 – Cisco NGFW Reference Architecture
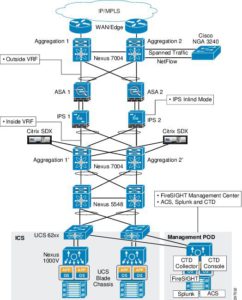
Figure 4 – Cisco NGFW Traffic Flow
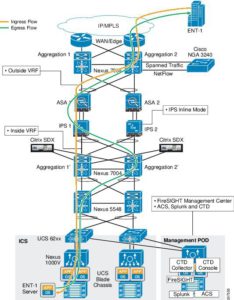
(Image Courtesy of Cisco) (Cisco Systems, 2016)
Conclusion
As you can see by the network diagrams shown in Figure 4, understanding traffic flow in and out of a Data Center or Cloud environment is quite complicated. When you add Contexts, NAT/PAT Rules, Layer 7 Rules, Rate Limiting of certain types of traffic and URL Filtering, the configurations became extremely complex. While mission Critical traffic might be allowed to traverse some links, NGFW’s also introduce problems in a network. E.g. Asymmetric routing of traffic over active/active links, reordering of TCP sequence numbers when performing Network or Port Address Translation NAT/PAT) on traffic from an outside public interface to an inside DMZ or private interface.
More than anything, NGFW that utilize Application Visibility and Control (AVC), Intrusion Prevention Systems (IPS), Advanced Malware Protection (AMP), and URL Filtering are a necessity.
References
Cisco Systems. (2016). Retrieved from http://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Data_Center/VMDC/Cloud_Security/1-0/DG/ICSecurity/ICSecurity3.html
Gordon, A. (2015). Official (ISC)2 Guide to the CISSP CBK, Fourth Edition, 4th Edition.
IS Buzz News. (2017). Retrieved from http://www.informationsecuritybuzz.com/isbuzz-expert-panel/cia-triad-and-new-emerging-technologies-big-data-and-iot/
KrebsonSecurity. (2013). Retrieved from https://krebsonsecurity.com/2014/02/target-hackers-broke-in-via-hvac-company/
Tech Target. (2017). Retrieved from http://searchsecurity.techtarget.com/definition/polymorphic-malware
2 comments on “Next-Generation Firewalls: Intelligent Threat Analytics in Cyberspace”
Comments are closed.





Nice post. I do think it is interesting that we frequently talk about user error as a source of openings for attackers in the sense of the people using the software being careless. The fact that many of these openings exist because of careless programming or a hole in a validation plan is a very similar type of human error on the production side of things.
I had never heard the term polymorphic used to describe malware before, very interesting. I had read an article recently about “frankenstein” malware. The concept is similar except that “Frankenstein forgoes the concept of a metamorphic engine and instead creates mutants by stitching together instructions from non-malicious programs that have been classified as benign by local defenses.”
https://www.usenix.org/conference/woot12/workshop-program/presentation/mohan
As our computers and program get more and more complicated these attacks are getting intricate to the point that it seems unreasonable to think they can all be headed off without any impact. As you highlighted with the cisco traffic flow these systems are complicated and even if they are designed with security in mind (which many now are) there are likely to be holes of some kind. This is why I am particularly interested in the methods of isolation and quarantine Dr. Stephen Herrod mentioned, where instead of assuming we can keep everything out we create safeguards to minimize damage once something gets in.
Users who have LIKED this comment:
Hi Kyle. Thanks for the insightful response. I work in the field as a Cybersecurity architect for several federal organizations. You would not believe how many derivatives of malware and other malicious code exists out there. Cisco and Palo Alto Networks use their sandboxing methods to execute code in a hypervisor. They often create thousands of dynamic signatures every day to block new threats. While there seems to be a decline in the amount of malware out there, it’s really going to depend upon how AI and ML get implemented into threat intelligence. As threat and defense networks become smarter, it will become more difficult for hackers to create malware that isn’t detectable by intelligent algorithms in the cloud that run scans against packets. This is another reason why, as Dr. Herrod pointed out, it’s a promising idea to put your data in the cloud
https://www.gdatasoftware.com/blog/2017/04/29666-malware-trends-2017
Users who have LIKED this comment: