
Mobility and IoT (Internet of Things): CyberSecurity and Threat Prevention
Technology Evolution
As 802.11 Wi-Fi networks have become more prevalent within the industry, Mobility Applications and IoT (Internet of Things) devices are being developed and evolving at a spectacular rate bringing us closer to connected and more intelligent networks. As of 2008, “the number of things connected to the Internet surpassed the human population. The adoption rate of the IoT is trending to be at least five times faster than the adoption of electricity and telephony” and will reach 50 Billion devices by 2020. [1]

As an industry expert in 802.11 technologies, I have seen the evolution of Wi-Fi connected devices first hand. Initially, there were connected devices for home entertainment purposes like the Sony PlayStation, Microsoft Xbox, and the Apple TV, which allows users to stream digital carnage at the touch of a button. Eventually, home entertainment consoles became a necessity for most, connecting people to Netflix, HBO and other providers of streaming media. From the early 2000’s, these types of devices became common in many households due to their ease-of-use and the convenience they provided.
As human beings, we have an insatiable need for technologies that make our lives easier, whether it’s a GPS built into our vehicle or an application running on our Smart Phone connecting us to Facebook, Instagram or an application that allows us to get from point A-to-B (Uber, Lyft) we have become reliant on our Smart Phones and the underlying technologies.
CyberSecurity and Threat Prevention Mechanisms
As Wi-Fi and mobile technologies have evolved, scalable addressing schemes like IPv6 (Internet Protocol version 6) have become more popular. “IPv6, a foundation of the IoT, is subject to the same attack threats as IPv4, such as smurfing, reconnaissance, spoofing, fragmentation attacks, sniffing, neighbor discovery attacks, rogue devices, man-in-the-middle attacks, and others.” [2] [3]
Network manufactures like Cisco have forecasted that IoT is the next emerging technology that will revolutionize the industry and change how we interact with our environment. [4] As we move towards a more connected IoT world, CyberSecurity has become a very important consideration for any organization and/or consumer that is interested in protecting their information, identity and even their life.
Like many networking companies, Cisco has invested millions of dollars in IoT research and development. Cisco understands that CyberSecurity is a very important aspect of the IoT market and securing IoT devices and device analytics is paramount.
As 802.11 Wi-Fi networks have become more widely deployed, many enterprise and state wide medical organizations have adopted the use of security appliances (Cisco ISE, Aruba Clear Pass) that facilitate the implementation of security policies for mobile BYOD (Bring Your Own Device) and for profiling and securing IoT devices within healthcare.
In addition to consumer devices, there are several IoT devices being developed within the biomedical industry that rely 802.11 Wi-Fi and other wireless technologies and are absent the appropriate security mechanisms.
For Example:
“St. Jude Medical implantable cardiac devices (pacemakers, defibrillators, and resynchronization devices) provide pacing for slow heart rhythms and electrical shock or pacing to stop dangerously fast heart rhythms. These cardiac devices are implanted under the skin in the upper chest area with connecting insulated wires called “leads” that go into the heart. A patient may need an implantable cardiac device if their heartbeat is too slow (bradycardia), too fast (tachycardia), or needs coordination to treat heart failure.
The St. Jude Medical Merlin@home Transmitter uses a home monitor that transmits and receives RF signals used to wirelessly connect to the patient’s implanted cardiac device and read the data stored on the device. The transmitter, located in the patient’s home, sends the patient’s data to his or her physician(s) via the Merlin.net Patient Care Network using a continuous landline, cellular, or wireless (“wi-fi”) Internet connection.
Summary of Problem and Scope:
Many medical devices—including St. Jude Medical’s implantable cardiac devices—contain configurable embedded computer systems that can be vulnerable to cybersecurity intrusions and exploits. As medical devices become increasingly interconnected via the Internet, hospital networks, other medical devices, and smartphones, there is an increased risk of exploitation of cybersecurity vulnerabilities, some of which could affect how a medical device operates.
The FDA has reviewed information concerning potential cybersecurity vulnerabilities associated with St. Jude Medical’s Merlin@home Transmitter and has confirmed that these vulnerabilities, if exploited, could allow an unauthorized user, i.e., someone other than the patient’s physician, to remotely access a patient’s RF-enabled implanted cardiac device by altering the Merlin@home Transmitter. The altered Merlin@home Transmitter could then be used to modify programming commands to the implanted device, which could result in rapid battery depletion and/or administration of inappropriate pacing or shocks.” [5]
Hacking Mobile Applications and IoT
Imagine for a moment the potential damage that could be caused by a hacker unlocking a IoT connected door lock (August Smart Lock)[6] or hacking someone’s IoT camera system and gaining access to their microphone (Amazon Echo Look); or even worse, hacking a Baby Monitor [7] or Wi-Fi controlled medical device that is connected to someone heart. As you can imagine, Cybersecurity takes on a whole new meaning when the IoT device provides us with some type of physical security, or monitors our health.
Summary
In the first lecture, Chris Cruz, CIO in the Department of Technology for California indicated there are 39 million people in the State of California, where 14 million users have mobile devices in which information would be accessed. During his lecture, he elaborated on the millions of threats that are detected by California State networks every day and how the State reacts to cyber threats and which Federal organizations they interact with through the use of their Sacramento-based Data Center. [8] As more organizations move their on premise resources to the cloud, it’s important to understand that organizations are not restricted to the use of Microsoft or Amazons Cloud Security and that enterprises have the ability to utilize VM (Virtual Machine) based images provided by vendors such as Cisco [9] or Palo Alto Networks [10] where a Next-Generation Firewall can be deployed and connected to a vSwitch providing Intrusion Prevention, Advanced Threat Detection (Malware), and immediate sand boxing of potential threats to secure Mobile and IoT computing.
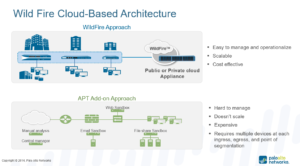
[11]
According to Cisco’s security model, this begins with using Authentication (Encryption), Authorization (Profiling), Network Enforced Policy (utilizing secure protocols) and Secure Analytics in the Cloud providing Visibility and Control over all connected devices. [12]
As we move into the future, it’s a very important consideration to ensure that IoT connected devices utilize an appropriate level of security to ensure that intercepted communications are not readable by third parties, and that IoT devices developed for use the biomedical industry utilize hardened security protocols.
References:
- http://www.cisco.com/c/en/us/about/security-center/secure-iot-proposed-framework.html#2
- http://www.cisco.com/c/en/us/about/security-center/secure-iot-proposed-framework.html#6
- Gont, F., “Security Assessment of the Internet Protocol version 6 (IPv6)”, UK Centre for the Protection
- http://www.cisco.com/c/en/us/about/consulting-thought-leadership/what-we-do/ioe.html
- https://www.fda.gov/MedicalDevices/Safety/AlertsandNotices/ucm535843.htm
- https://techcrunch.com/2016/08/08/smart-locks-yield-to-simple-hacker-tricks/
- https://www.rapid7.com/docs/Hacking-IoT-A-Case-Study-on-Baby-Monitor-Exposures-and-Vulnerabilities.pdf
- https://canvas.stanford.edu/courses/67124/files?preview=1938288
- http://www.cisco.com/c/en/us/products/security/virtual-adaptive-security-appliance-firewall/index.html
- https://www.paloaltonetworks.com/products/secure-the-network/virtualized-next-generation-firewall/vm-series
- https://www.slideshare.net/BAKOTECH/dell-joint-event-2014-november-onur
- http://www.cisco.com/c/en/us/about/security-center/secure-iot-proposed-framework.html#9
Users who have LIKED this post:
7 comments on “Mobility and IoT (Internet of Things): CyberSecurity and Threat Prevention”
Comments are closed.





Hello Christian,
I enjoyed reading your elaborate article, as it encompassed a complete view on technological evolution, including the growth of the use of IoT devices, the problems that may arise due to their cybersecurity vulnerabilities, and possible solutions to these problems. As the use and dependance on IoT devices increase, ensuring a level of security has inevitably become a necessity to the users of these devices. The growing importance of cybersecurity is evident when reviewing St. Jude Medical Merlin@home Transmitter, as you have stated in your article, for any alterations to the programmed commands may result in altercations to someone’s health. Though there are multitudes of cases that reveal the importance of cybersecurity, one that stands out among the rest is, I believe, the recent worldwide cyberattack known as the WannaCry ransomeware attack, which spread rapidly to infect hundreds of thousands of computers. The WannaCry ransomeware attack exemplified the dire consequences of the failure to provide the necessary level of security. With the sophistication of the attackers, security holes in the systems of businesses, and easy access to the hacking tools made available by the government, ransomeware attacks have become somewhat of a common sighting. Although the attack slowed within days of the initial outbreak, “[utilizing] an appropriate level of security to ensure that intercepted communications are not readable by third parties” is crucial to prevent the risk of an attack much greater in severity (Estes).
Users who have LIKED this comment:
Hello Joha,
Thank you for your response.
I enjoy discussing CyberSecurity topics and prevailing trends in the market.
WannaCry was a cryptoWORM that propagated using EternalBlue, an exploit of Windows’ Server Message Block (SMB) protocol. According to articles on the Independent and Telegraph website, the U.S. National Security Agency (NSA) had already discovered the vulnerability, but used it to create an exploit for its own offensive work, rather than report it to Microsoft. [1] [2] [3]
When I began digging deeper into the topic of Ransomware, I discovered variations in the reporting of Ransomware between OS vendors and providers of Anti-Virus and Anti-Malware software. (McAfee, Symantec, TrendMicro)
According to AV-Test, a leading international and independent service provider in the field of IT security and anti-virus research (https://www.av-test.org/en/), Ransomware has only attributed to 0.94% of all Malware in 2016 and the 1st QTR of 2017. [4] While it might be controversial to doubt Malware statistics provided about a Microsoft OS, Microsoft themselves are motivated to market the idea that using their Windows OS is relatively safe and not susceptible to so many attack vectors.
On the other hand, Anti-Virus and Anti-Malware companies like McAfee are motivated to sell their software and might report more conservative statistics to the market in an effort to convey the importance of using their products. Either way, the number of Ransomware attacks for both Windows and OSX operating systems has increased dramatically over the last two years and is a prominent threat according to both giants.
If we were to evaluate McAfee’s Quarterly Threat Report, we can see that that the “Total New Ransomware” has increased from just under 3M in Q1 of 2015 to just over 9M in Q4 of 2016. [5]
In the past, many users believed that moving to an Apple was safer, but we can now see the amount of Malware produced for Apple computers has also grown considerably. According to McAfee Labs, New Malware statistics (page 39) for Apple Computers has grown from < 5000 to over 450,000 through the use of Adware bundling. [5]
As IoT evolves and the idea of distributed and SMARTcomputing becomes more widely adopted, we need to be concerned about the propagation of Bots across IoT. If you’ve ever seen Silicon Valley, Season 4, Ep 10 Server Error, you will understand what I mean.
References:
1) https://en.wikipedia.org/wiki/WannaCry_ransomware_attack
2) http://www.independent.co.uk/news/uk/home-news/nhs-cyber-attack-edward-snowden-accuses-nsa-not-preventing-ransomware-a7733941.html
3) http://www.telegraph.co.uk/news/2017/05/13/nhs-cyber-attack-everything-need-know-biggest-ransomware-offensive/
4) http://zdnet2.cbsistatic.com/hub/i/r/2017/07/05/ae031638-343d-409d-b3b1-3bd942c6a7ab/resize/770xauto/755e2c4c7db07d7b9adae4d1fcd63b2f/av-testwindows.png
5) https://www.mcafee.com/us/resources/reports/rp-quarterly-threats-mar-2017.pdf
Thank you for your post. I enjoyed reading it and really liked your first graph (the growth of “Things that need to be protected.”)
Through my non-profit work, I get to engage with peer organizations (other foundations) around the most urgent topics we need to invest in. Cyber security is one of those critical topics. Last week, I had a meeting with a foundation that is trying to push the idea of adding a cyber security rating in Consumer Reports. They want to try that as a way to raise consumer awareness and put more weight behind it. I was wondering what you think about that idea?
Users who have LIKED this comment:
That sounds like an outstanding idea. I like the idea of rating how secure organizations are. It provides consumers with a threat rating of sorts. If you refer to the Target incident, in which hackers gained access to credit card numbers through a vulnerability in the HVAC systems. Target said that the breach exposed approximately 40 million debit and credit card accounts between Nov. 27 and Dec. 15, 2013.
It would be interesting to see how Threats are weighted by a consumer reporting agency and how an incident such as this could dramatically drop a rating from a high-score to a low score as the result of something like this.
https://krebsonsecurity.com/2014/02/target-hackers-broke-in-via-hvac-company/
Users who have LIKED this comment:
I appreciate the personal insight in this post, and you nicely address the scope of possible attacks . Other topics in this class and in emerging technologies center around seamless integration of X, and scalability of X, connectectivity/smart X or providing X as a service. With each success in these areas it seems that the trend is to consolidate user experience onto fewer and fewer isolated devices / applications (either that everyone uses the same service like the popular AWS for computing or that everyone’s thermostat is in contact with the same server / database …). Due to this trend it seems that though the possibility and prevalence of malicious attacks has always been present (hackers have been around for as long as computers have) the impact of just one of these successful attacks can be much more widespread and do much more damage. I would imagine that this is/will soon give rise to new methods of detection and quarantine (and unfortunately malware) with a focus on greater scale.
Users who have LIKED this comment:
Thank you for your insights into IoT and cybersecurity. As our dependence on IoT devices grows, their potential to cause significant damage to society grows as made clear by your discussion of St. Jude Medical’s implantable cardiac devices, the Hajime botnet (https://www.theregister.co.uk/2017/04/27/hajime_iot_botnet/), and the Mirai botnet (https://www.wired.com/2016/12/botnet-broke-internet-isnt-going-away/). While most of these devices can greatly improve the lives of their users, it is important to introduce regulation to mitigate safety issues and protect citizens and businesses. Nevertheless, there is a tradeoff between increasing regulation and stimulating innovation. Too much regulation could unnecessarily inhibit technological development in the United States. I wonder what your perspective is on IoT security regulation. Do you think the US government should require IoT vendors to ensure that their devices meet security standards? Do you think this is enforceable, i.e. can it be implemented? What actions should the government take to protect its citizens and businesses against IoT security threats?
Users who have LIKED this comment:
“I wonder what your perspective is on IoT security regulation. Do you think the US government should require IoT vendors to ensure that their devices meet security standards?” (Planque)
I think the government should keep their hands off the IoT and the Internet. While the NSA, DoD and DHS are always going to have their hands on encryption mechanisms to protect our national security, regulation of IoT will stifle innovation and biomedical research.
“What actions should the government take to protect its citizens and businesses against IoT security threats?” (Planque)
I don’t believe that should be our governments concern. I do think that Consumer IoT devices should be tested and rated to ensure they are safe around children or for biomedical use. I believe the responsibility lies with the manufacturer to test the products and the consumer to deploy intuitive application layer appliances (Firewalls, IPS, Threat Intelligence) to protect critical infrastructure.
As you know from being a CS graduate, Hackers will often deploy Bots to create large scale Botnets, which coincidently can be used to cause damage to critical infrastructure. Botnets have been known to perform DDoS (distributed denial-of-service) attacks, steal information from cookies (usernames and passwords), and allow attackers to remotely access devices to jump from one machine to another to further distribute malicious code.
If I were a member of the U.S. Cyber Command, I might be concerned with the standardization or use of IoT compute for malicious purposes. E.g. the creation/evolution of a “technological singularity” through distributed computing or as referred to it in the movie Terminator, (Skynet).