
Cybersecurity Incidents and How You Protect Yourself as a Student
Last Friday, Steve Harrod, Managing Director at General Catalyst, visited us in class and gave a talk on Cybersecurity. He brought up subjects such as the fact that the more connected our homes are, the easier it is for people to hack into our lives and how social media increases the risk of being hacked. Today, one in every three Americans get hacked each year and 18-24 year olds are the most likely to fall victims [1]. So as tech savvy students, we can and should protect ourselves, which is why I’m going to share a couple of tips that might help.
To think about when sharing – offline.
Information on your physical devices such as your phone or computer is the easiest to access when the device is in the hands of a hacker. Because of this, it is important to keep your physical devices in safe storage when you don’t have them with you. If you live in a residence where people pass by, don’t let them lie out in the open when you’re not there.
It is also important that you keep your passwords to yourself. Even your best friend shouldn’t know them. Make sure to not write your passwords down anywhere, you can use a software such as 1Password or LastPass to help you keep track of your passwords instead. Another password tip is to make every password unique, and make them difficult to guess. This means no pet names, no birthdays and no 1234s. If you can use two-factor authentication, do that!
To think about when sharing – online.
We all know Snapchats disappear after 10 seconds, but a push of two buttons and someone has saved it forever, so make sure you only share content you’re comfortable with being in someone else’s hands. Because as the saying goes; Internet never forgets.
Social media is a common platform to share what we love, and it’s a great way to keep in touch with our friends. But as soon as information is public, anyone has access to it. More and more common are cyberattacks where someone pretends to be a person you should know because of common interests or because you attended the same school. As we share more information like this on Facebook, LinkedIn and Instagram, scammers can more easily manufacture identities that we could trust.
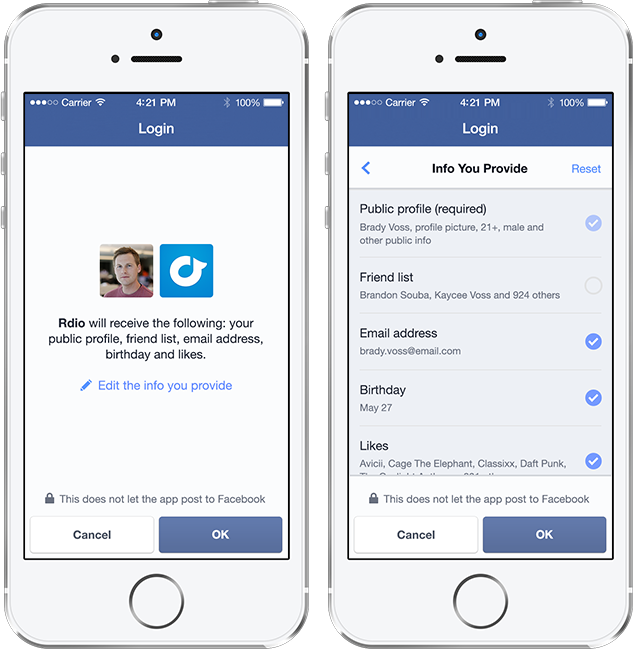
If you want to go even further, I would recommend to not use Facebook for signing up on new websites. The convenience of this option is great, but companies actually get much more information about you from Facebook than you would think (and might want). However, if convenience is important to you, you can click Edit in the Permission screen the next time you sign up with Facebook, and you’ll be able to see exactly what data is shared about you. Here you can also choose what information you don’t want shared with the company.
To think about when you get an email.
The odds are high that you’ve already received a phishing email, asking you to update your credit card information or your password, looking like it’s from a provider you’re using or someone who says they went to high school with you.
There are some things that you can keep an eye out for in these kind of emails. The obvious ones are of course when you don’t know the service or the person who’s sending the email – and that the email is flat out poorly designed or has misspellings. Other than that, look at the Sent from email address. If the email “pretends” to be from The Service, the from-address will end with something else than @theservice.com.
Another sign is that the introduction says “Dear The Service member” or “Hi The Service customer”. This is very generic and is used by scammers to trick you. Usually these services know your first name, however, and they would use that in the introduction.
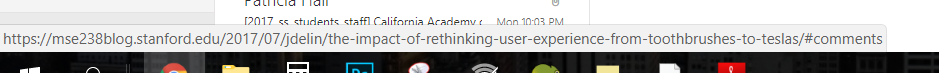
The last trick to use is to hover any clickable image or text and check where it would take you. If it’s not to theservice.com/… then you should be not click it. Depending on your browser, you can check the hover link in the bottom left corner or by right clicking on the link.
To think about when you’re on a website.
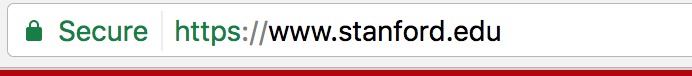
There are a few other details that can be important to keep track of. And you don’t have to be technical to understand them. One of them is “the https”. If you find yourself on a website where you need to register any private information, such as banking or credit card, check that the domain starts with https, not only http, and that there is a little green lock on the left of your domain.
If a website doesn’t have this, it means that the information that gets sent between the website and the server, isn’t encrypted. And that’s bad. Because that means it’s much easier for a hacker to get ahold of the information you’re typing into a website.
References:
Principal Offensive Security Consultant at Cybersecurity organization
[1] https://www.munichre.com/HSB/hack-survey/index.html
https://www.financialsafetynet.org/college/cyber-security-tips-for-college-students/2437
https://www.visitorpasssolutions.com/Blog/4-cyber-security-tips-for-students/
https://blog.lastpass.com/2013/09/cybersecurity-tips-for-college-students.html/
5 comments on “Cybersecurity Incidents and How You Protect Yourself as a Student”
Comments are closed.



Hi Julia,
I thought your essay was very well written and direct. I liked many of the points you brought up. For instance, I thought it was very interesting that if you sign into a website using your Facebook account, that website then has access to much of your personal information. Thus, thousands of websites have very personal information on millions of users, all in the name of optimization of marketing and sales. Although I agree with the bulk of the tips you offered, I found one a bit hard to swallow.
You recommended a strategy of keeping multiple unique passwords for various sites, which I believe makes sense. But you then suggested signing up for password management services like 1Password or LastPass to store and keep track of all of these passwords. I believe that the usage of password keeping software can be dangerous because it requires that all of your valuable information must be placed on the web in one central location. Therefore, if someone were to hack the password management service, all of your information could be exposed. For this reason, I plan to commit these passwords to memory and also always require two-step authorization.
Hi Aristotle,
I think you make a great point, this is of course the safest way to go about. However, using unique passwords for every site will soon add up and you’re memory will probably fail you (and your inbox will only contain “forgot password” emails). And clearly, the safest option isn’t the password keeping softwares, because as you mention, they are also in the cloud – and therefore vulnerable. I’m looking forward to more services moving towards other ways of logging in, such as Medium that has email login, which they talk about in a 3 min-read blog post here that I recommend: https://blog.medium.com/signing-in-to-medium-by-email-aacc21134fcd
As they say: “Passwords are neither secure nor simple. They’re hard to remember or easy to guess, everyone re-uses them (even though they know they shouldn’t), and they’re a pain to type on mobile. They don’t even keep you that safe.” which pinpoints the issue quite well.
The question is, what is the best solution that can be made? Will be interesting to see!
Oh hey there again!
I do agree with Aristotle on that one as I too, would never trust a 3rd party site to keep my passwords. I think no one should have any ideas, tips or hints regarding where your password would start with and thus I personally wouldnt give in to that. For all we know, that could be a hacker acting as a, ‘legitimate’, 3rd party website.
Further I would like to explore the ways worded passwords are outdated. With the technology these days, I feel that there are other ways in order to protect your accounts. Arguing this, biometrics is seen to prove further detail into encrypting individual characteristics which enables users to disposes the need for passwords. Accuracy increases and impersonation is harder to crack.
What makes biometrics so special is that they are industry agnostic. No matter the technology or device, for example, fingerprint readers, retinal eye scanners, voice recognition systems, hand geometry, facial recognition, or even a new, “selfie”-based authentication method that MasterCard and USAA have introduced. The idea is to verify someone’s identity with a high degree of assurance by tying it to multiple mechanisms at once. This is known as biometric modalities. These modalities, when in action, can provide a significantly safer environment for the customer and are much simpler to use.
Biometrics are also harder to manipulate than passwords and other two step verification processes. While a bad actor could possibly gain access to your thumbprint on the specific device it is stored on or to your digital voiceprint, if an app simultaneously requires a thumbprint, a retina scan, and a vocal recognition signature, it would be almost impossible for a bad actor/ hacker to replicate that in the seconds needed to open the app.
While this system is a much safer alternative to passwords, executives who are engineering new digital products, apps, and websites will need to find the right balance between security requirements and user experience. This is easier said than done, especially in an environment where customers expect to be able to interact with your product on multiple digital devices.
According to a study, 68% of users reuse passwords, and of this 90% will change a few words, numbers and figures in aim to have a similar password to their past. Coming from experience I myself do this and am afraid that hackers can read this post and or Julia will hack me in the near future!!
The majority (69%) of Americans think having their personal information stolen in their lifetime is inevitable, and 84% feel their personal information is more vulnerable now than a year ago.
Password based authentication is no longer capable of meeting the demands of modern information security, according to a survey of 589 consumers by LaunchKey. And similarly to what you said, an overwhelming amount of 84% of respondents support eliminating passwords all together, while 75 percent said they forget passwords or have to write them down.
Thanks Julia, see you this weekend 🙂
References
https://www.wired.com/2012/11/ff-mat-honan-password-hacker/
http://fortune.com/2016/05/12/biometrics-passwords/
https://techcrunch.com/sponsored/forget-passwords-how-biometrics-are-transforming-the-security-of-mobile-payments/
This is a very informative post, Julia! I’d like to add one more thing. I have come across a lot of people who download mobile applications from the App Store and Google Play Store without fully reading the information the app can access once downloaded. Some applications access information that isn’t necessary for it to function. For example, a voice recorder app I downloaded on my Android phone was able to access my contacts, location, email account details and even my photos. That said Apple has developed a good method to ask user permissions before the app can access a particular type of information but this was implemented only recently on Android phones. However, we should all be aware of these app permissions and manage them properly.
Hi Julia
Happy to discuss this topic!
Students are the most prone to cyber issues and this is not because they are careless, we all are… this is primarily because of the lack of understanding about the pros & cons of cyberspace, the biggest issue we face in today’s world is absence of cyber world education in our schools. imagine you are left on a remote island without any formal training in art of survival !!! all kids get trained on the real world basics like crossing the road or manner for that case etc but there is no formal training given for life in cyber space which is the root cause of all issues students face today… there are cyber staking group who track and identify the most vulnerable victims basis the information shared by them on various platform, hacking profiles are made and all this is done in a very professional way. these profiles are been sold to hackers or cyber blackmailers who then use this information to commit the crime. on emails it does not help if you check the ‘from’ address to verify the authenticity as this can easily be masked. Most https links are hackable and this is due to the number of service providers in the market, these guys build certificates using standard resources (most of which are available as open source) but dont bother to customise or update the encryption layers. for the passwords – it does not matter how complicated your password, what matters is the length of the password, more the characters more the combinations for the hacking program to crack. so ideally your password should be a lengthy combination of words, numbers and characters. Off-course biometric is by far the most effective means to authenticate but the issue is it rely on hardware, most of the high end phone today have finger print scanners but still the majority lack this feature (most of the high end laptops and desktop still dont have this feature). Voice authentication AI is fairly new and difficult to implemented due to its complex nature. We still dont have a very dependable technology which can be implemented on mass scale for iris or face recognition.